Open Source projects depend on an active community of users and developers to contribute their time and skills to improve individual projects and the open source ecosystem in general. All users can contribute to Ubuntu by using Apport to report bugs for fixing.
Ubuntu uses
Launchpad for bug tracking and
Apport for bug reports. It is designed to be easy for the user as it collects info about the OS, running processes and hardware during crashes. You don't need to be able to reproduce the bug to provide useful information for the developers.
Generally Apport supports two types of bug reports:
1) Launched when you experience a crash. Automatically opens apport and walks you through the reporting process.
2) Initiated by the user when bug is noticed during use of a program but does not cause a crash, for example an application option that does not work as expected or a problem with the user interface.
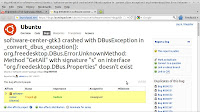
When a crash occurs Apport creates a persistent and detailed crash report in /var/crash which can be used to determine the problem, even for bugs which are difficult to reproduce. This report contains detailed information about system state and installed software. Apport uses package hooks to collect additional information from log and configuration files.
Sometimes crashes can be hard to attribute to a specific program or service so Apport uses the
apport-symptoms package symptom based bug reporting. The UI guides the user through selection of symptoms and uses question and answer scripts to locate the offending package and determine what data to collect.
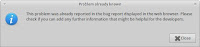
Bugs which affect large number of users may have already be reported many times and this can cause unnecessary work for developers and users. Apport uses 'Bug Patterns' to recognize specific recurring errors and instead of filing a new report, takes the user to the Launchpad bug page where they can review previous reports and determine if this a new or known bug.
Bugs in X drivers, sound and the kernel should always open a new bug report to be sure your hardware is included in any fix.
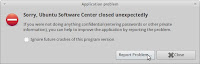
Following a program crash, a message will appear offering to help you report the problem. If you were entering confidential information when the crash occurred you should click 'Cancel'.
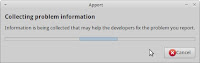
Most of the time crashes occur when you are performing routine tasks and these should be reported. Click 'Report Problem...' to begin collecting information about what your computer was doing when the crash occurred.
Apport will ask to 'Send problem report to the developers?' Click 'Content of the report' to view the data apport has collected or you can open the plain text document in /var/crash. If you would like to file the report later, you can navigate to this report and double click on it. Apport-gtk will open allowing you to file the bug report.
Click 'Send Report' to upload the report to Launchpad's bug tracking system. Your browser will launch and you will be directed to Launchpad to login or create an account. You are then taken to the packages' bug filing page.
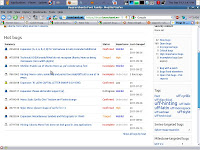
Look over the list of 'hot bugs' and see if your bug is listed there. If the problem has been previously reported, click on 'Mark as Duplicate'. If it is a new bug, click 'Report Bug'.
Briefly describe the the problem and what caused it, if known. Launchpad will search for similar bug reports. If none are found to match your problem, you will be asked for further information. Be sure to include what you were trying to do, what actually occurred and the steps to reproduce the problem, if known.
If the bug is a security risk, click the box 'This bug is a security vulnerability.'
Click 'Extra Options' to add tags to this report, attach files such as logs or screen shots or even submit a patch for the bug.
When finished, click 'Submit Bug Report'.
Apport is launched automatically when a crash occurs as a result of segmentation violation, bus error, floating point exception, etc, but sometimes bugs occur in more minor ways that will not trigger apport. For example perhaps you find a menu item which does not work as expected or problems with the interface. These may not crash the program but need to be reported so they can be fixed.
First go here and check if a specific bug has already been reported for your version of Ubuntu.
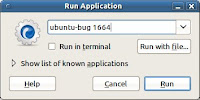
Use Alt+F2 to open the 'Run Application' window and type ubuntu-bug <package name> or for a running application, open your System Monitor (System > Administration > System Monitor) and note the process ID number. Enter the process ID into Run Applications instead of the package name for example, 'ubuntu-bug 1664'.
When should you not report a bug? Bug reports are not for support or feature requests or non-Ubuntu packages.
Even small bugs can make software seem unfinished and immature. Each bug squashed contributes to the overall quality of all open source software and enhances its' credibility with the public.
Filing bug reports is an important part of being an involved member of the Linux community. Apport makes it simple to do your part.
This article was originally published in UbuntuManual.org on Sept. 30, 2011























